Divine Info About How To Prevent Arp Attack
How to prevent arp poisoning.
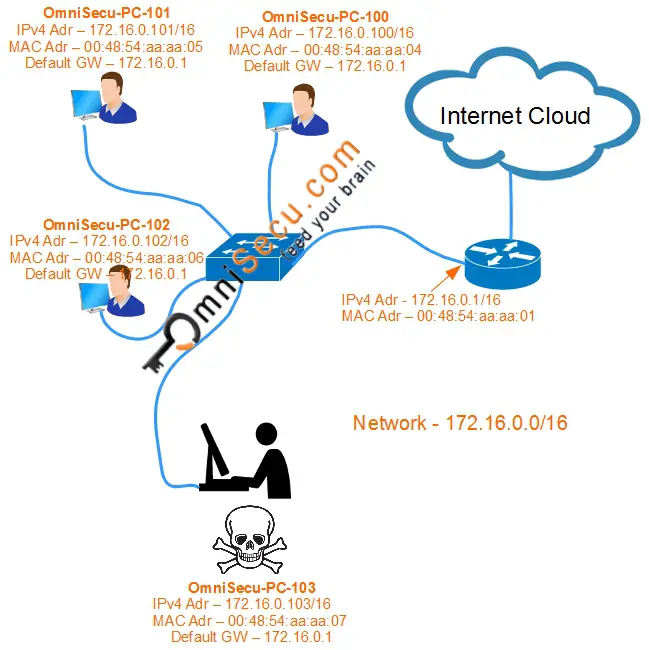
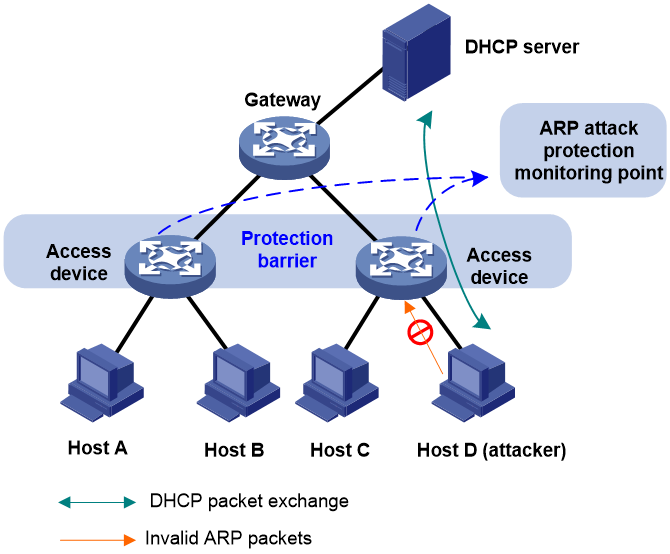
How to prevent arp attack. This article will explain arp poisoning techniques, its results, and how to prevent such attacks. Connected the dhcp server to the switch. With arp poisoning, a cybercriminal can redirect your.
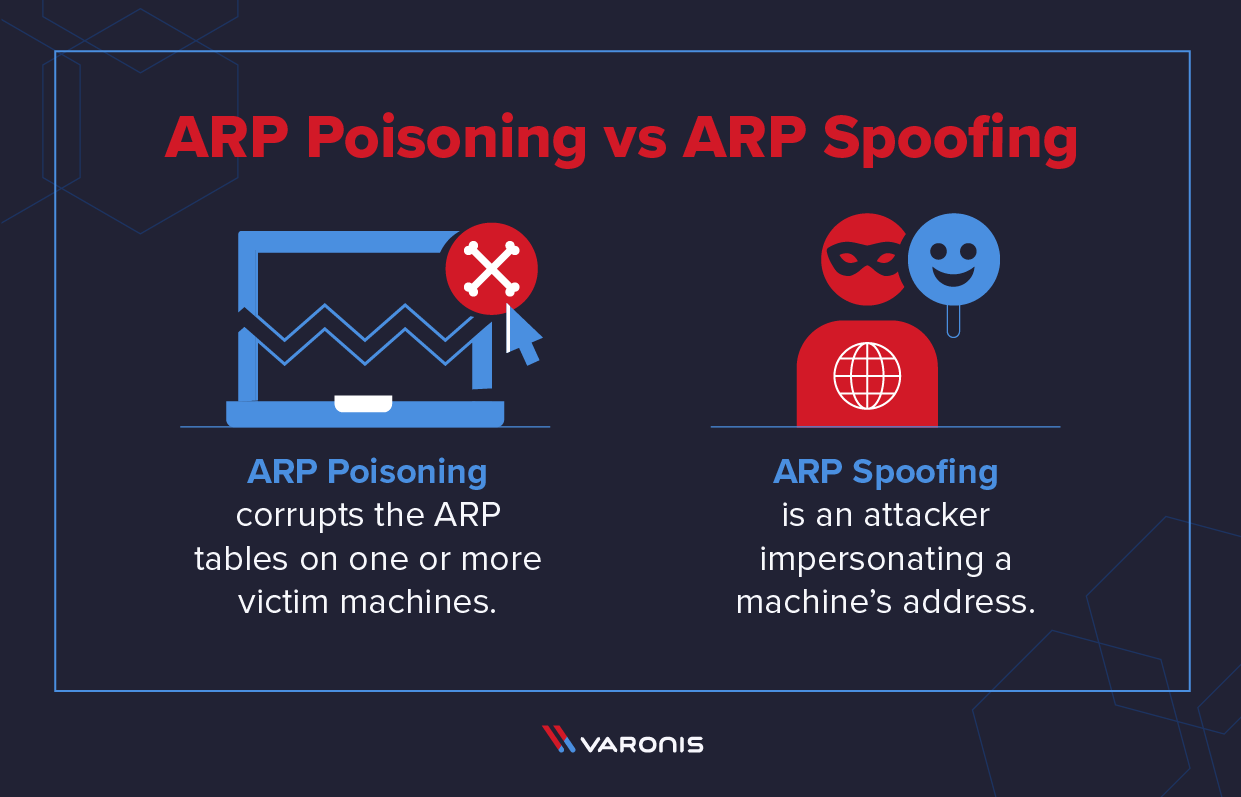
Address resolution protocol (arp) is a protocol that enables dynamic ip addresses to connect to physical media access control (mac) addresses to. In the first place, the attacker must have access to the specific local area network (lan). Assign static tcp/ip properties on your computer manually.
They scan the network to determine the ip addresses of at least two devices—let’s say. How to protect your network from arp poisoning in simple steps comes down to implementing simple protective measures to. With the widespread use of ssl/tls encryption on the web, this type of attack has.
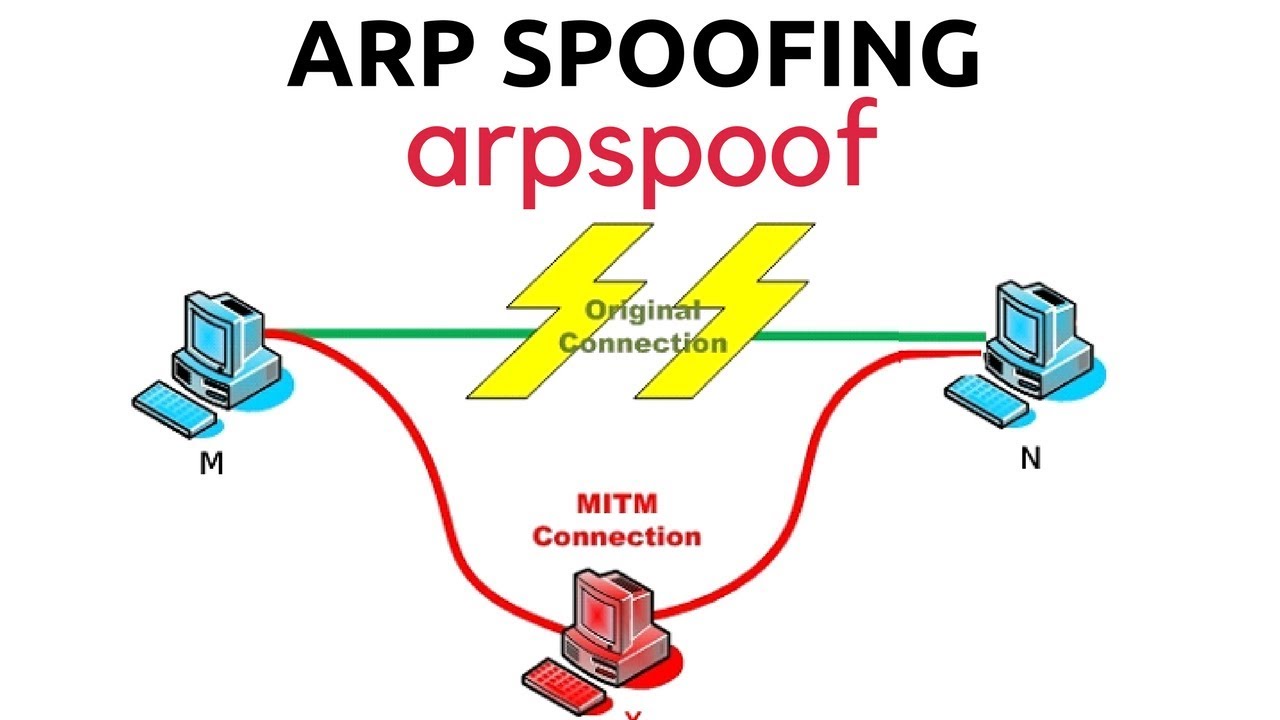
Please go to our website and check configuration for how to configure tcp/ip properties of my computer. Address resolution protocol (arp) spoofing, also referred to as arp cache poisoning or arp poison routing, refers to an. One way to prevent arp spoofing from happening in the first place is to rely on virtual private networks (vpns).
Please go to our website and check configuration for how to configure tcp/ip properties of my computer. Arp poisoning is a technique used for conducting various attacks within local area networks by exploiting the address resolution protocol. Click security > arp attack protection.
Rely on virtual private networks. The attacker must have access to the network. Open the web browser and type the lan ip address of the router in the address bar, the default ip.
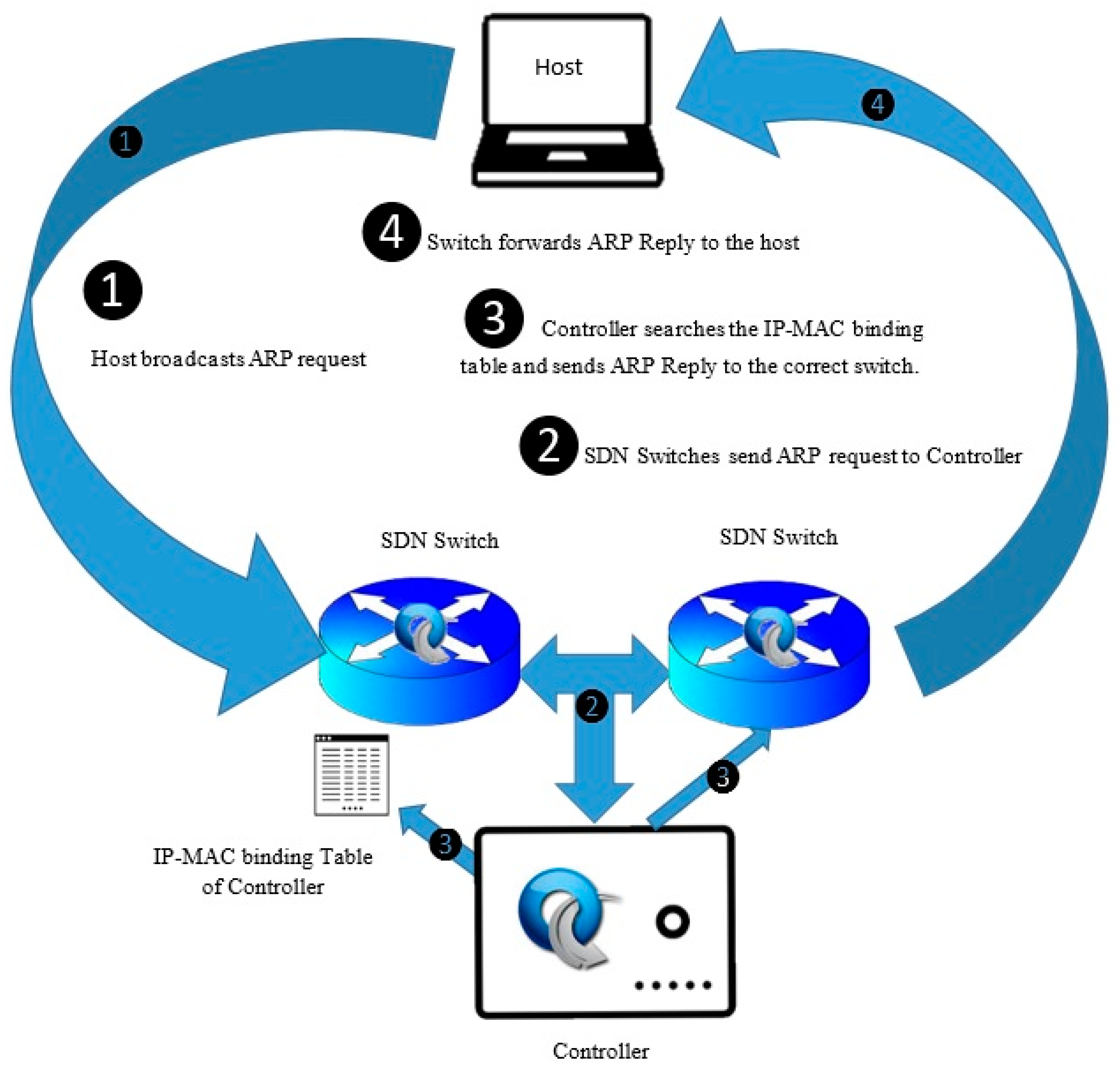
Before you configure dhcp snooping and dai (two port security features) to mitigate arp spoofing attacks, be sure you have: One viable way to prevent arp attacks is to use static arp as such an arp stop device to access or process arp responses are linked with that ip address. Open the web browser and type the lan ip address of the router in the address bar, the default ip.
The attack works as follows: They perform network scanning in order to acquire the ip addresses of. How to set on the router to prevent arp cheat?
Hiding behind legitimate networks through techniques such as arp poisoning attacks makes their jobs easier. First and foremost, a target is selected. The arp attack protection page opens.
The steps of an arp poisoning attack can change but generally, it has the following steps: A popular use of mitm attacks was to capture login credentials that were once commonly transmitted in plain text. Here are seven key ways to enhance your.